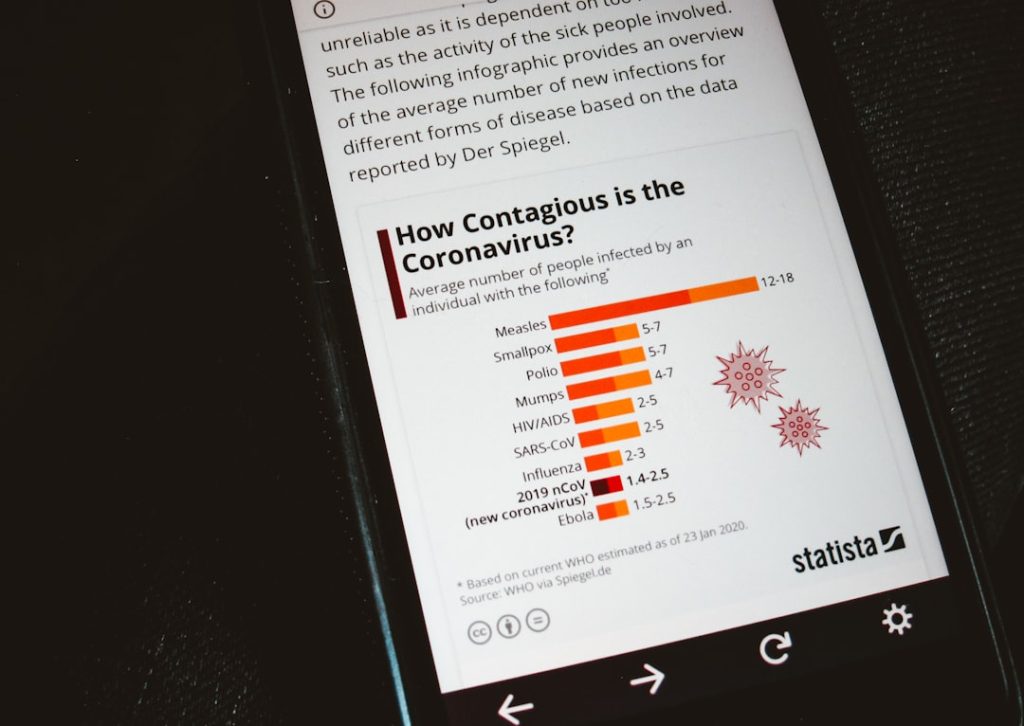
How to Delete Your Character AI Chat History Completely
In the age of AI-driven conversations, our interactions with platforms like Character AI can be deep, personal, and sometimes even a bit revealing. Whether you’re using it for fun, exploration, or support, there might come a point when you decide you want to delete your chat history for reasons such as privacy, security, or simply …